I have an email newsletter called Unlimited Leave where I write about AWS Management and Governance at scale.
The idea behind the name is to build systems, processes, and policies in AWS that enable the autonomy of developers, reporting for InfoSec, and scalability of work. Things that allow you to take carefree time off and reduce work on your nights and weekends.
Among all of the AWS Announcements, I primarily focus on the ones that come off of the Cloud Operations and Migrations Blog.
My shtick is all about how to manage, govern, and secure many AWS accounts at scale across multiple AWS Organizations.
If you are interested, you can subscribe here: https://newsletter.unlimitedleave.com/subscribe.
A couple of weeks ago I received a question from a reader regarding the use of the Control Tower. With the reader’s permission, here is his question:
Hi,
Thank you for your newsletter, I have been finding it useful.
I see you are asking us dear readers a question, but instead, I’d like to ask you a question. I have been looking at implementing Control Tower off and on again, but I’ve never really found it compelling enough to put it in the good ‘ole backlog. Maybe I am missing something here. My organization is using AWS SSO with an external identity provider and also at this point has a pretty static number of AWS accounts. We are also using Terraform to deploy a good amount of our infra. Could you say what benefit Control Tower brings compared to, say, just putting the controls in Terraform? Are there controls that there are no APIs? Maybe this would be covered in your Terraform module, but it’s definitely something I’m interested in learning about.
I responded directly in the email but promised a more detailed write-up of Control Tower and provide a compelling reason why an organization should use it (or not). Here it is.
Why use Control Tower?
A very solid question and a very polarizing one in certain circles in fact. I have, and still do share the sentiment on “Is Control Tower right for me/us.”
The quickest response to that question is – “it depends.”
The benefit derived depends squarely on what your organization is hosting and who/what you are beholden to when it comes to the data you possess.
The question isn’t necessarily about Controls but more about Governance. Who has a thumb on you, and how do you keep a thumb on developers or teams in your AWS Organization(s)?
In other words, do you report to or care about any multi-letter agency’s opinion of your environment?
Do industry standards and security frameworks matter when it comes to the workloads and data you are hosting?
Do any of these acronyms cause your hair to stand on end GDPR, PCI, SOC, HIPPA, FedRAMP, and so on?
Governance is about ‘allowing’ and ‘enabling’ when total control isn’t the desired outcome or is impractical. Configuring your AWS Organization with Control Tower helps accomplish this.
So what is AWS Control Tower
It is hard to argue that AWS Control Tower (CT) is a traditional AWS service. CT as a service isn’t a service at all. It is a Click-Next style wizard for setting up accounts using a ‘Vending Machine’ Model.
The service is just an administrative dashboard that incorporates multiple AWS Management and Security services into a single Console and has very little API/CLI functionality itself.
Think of an Air Traffic Control Tower orchestrating everything going on down on the airfield (Landing Zone), taxiway, and all of their responsible airspace. The need to organize, secure, deploy, track, authenticate, and comply.
With CT, the backend is a series of API calls to all of those services:
-
Organizations
-
Service Catalog
-
CloudFormation StackSets
-
Lambda
-
Config
-
Security Hub
-
S3
-
Identity Center (formerly AWS SSO)
This is important to realize when deciding if you should start with, or migrate to CT. Your organization will not gain any functionality that you couldn’t implement directly with any of the services listed above or that you already have implemented.
Marketing Speak (as written by AI)
Managing multiple AWS accounts can be a daunting task, especially when it comes to maintaining consistent security and compliance standards. AWS Control Tower is a powerful solution that helps you govern your multi-account AWS environment, providing a central place to set up and manage your accounts, resources, and policies. Here I’ll discuss the top three reasons why you should consider using AWS Control Tower.
Simplified Account Management
AWS Control Tower simplifies the management of multiple AWS accounts by providing a single place to set up and manage accounts, users, and policies. With AWS Control Tower, you can quickly create new accounts with pre-configured resources and permissions, allowing you to deploy new workloads faster. Additionally, AWS Control Tower provides a consistent account structure across your organization, ensuring that all accounts are set up with the same security and compliance standards.
Enhanced Security and Compliance
AWS Control Tower helps organizations achieve better security and compliance by providing a set of pre-configured guardrails that automatically enforce security best practices and compliance standards. These guardrails include policies for identity and access management, logging and monitoring, networking, and data protection. With AWS Control Tower, you can rest assured that your AWS environment is configured to meet best practices and compliance standards, reducing the risk of security breaches and compliance violations.
Cost Optimization
AWS Control Tower provides cost optimization features that help you manage your AWS environment more efficiently. For example, AWS Control Tower provides a pre-configured AWS Landing Zone that includes a set of pre-approved AWS services that are optimized for cost and performance. You can use this Landing Zone to quickly deploy new workloads, ensuring that they are set up with the right resources and configurations to meet your performance and cost requirements. Additionally, AWS Control Tower provides cost optimization guardrails that automatically monitor and optimize your AWS environment to reduce costs and improve performance.
What is life like outside of the CT brochure page? (as written by me)
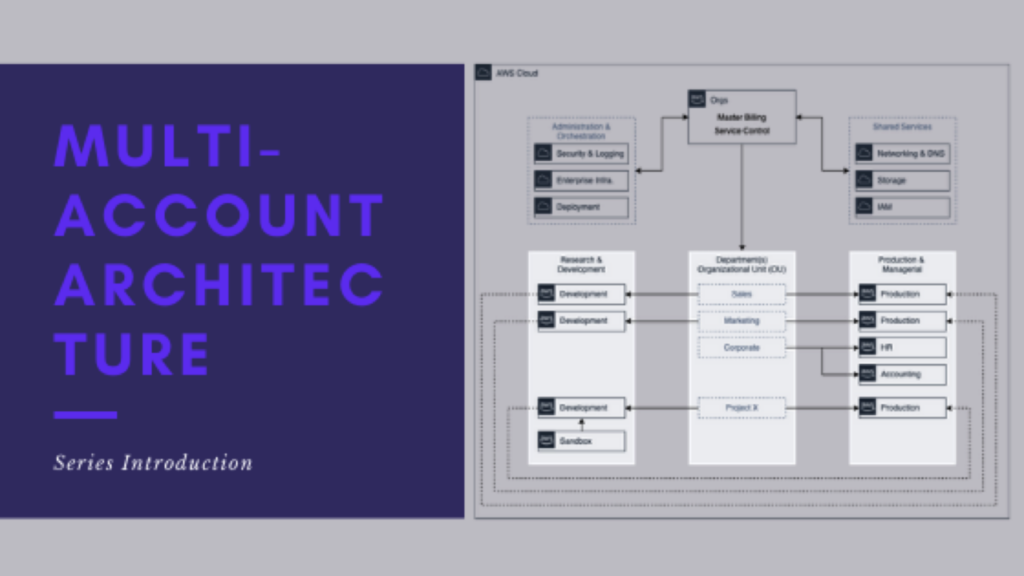
I’m pretty opinionated when it comes to how teams should manage their AWS Organizations. First, one AWS Organization is never enough. Two is the minimum for reasons I’ve laid out in “My Case for Multi-Org”.
Beyond that argument, an AWS Organization should be your boundary. Even if not all accounts in the org are considered in scope. Think of the structure as a vein diagram.
How to accomplish this is by using Control Tower.
Advantages of Control Tower
The advantages of CT are many. One is that CT in a brand-new organization will set up central logging of all accounts to a protected location just by enabling CT. All new accounts will get a CloudTrail Trail enabled and offloaded to an S3 bucket in a separate account that can be protected.
In addition, CT will configure AWS Config to monitor core best practice configuration and give you a dashboard to enable preventative and detective controls across all accounts in an organization. Beyond that, CT will protect those configurations so even Administrators at the individual account level cannot modify them.
These things of course can all be done without Control Tower:
-
the delegation of Security Services
-
enabling Config and Central Aggregator
-
implementation of SCPs
-
New Account Creation
-
Bucketing (OUs) of account types
Some of these still need to be done with API calls or in the Console but for the most part, the major items are done with Control Tower.
You could do all of this on your own, but you’d have to build that all yourself, and it’s not supported except by you. AWS versions all of this in what is called the Landing Zone version.
Is there a downside?
There is a downside to using Control Tower natively.
That is, you have to understand what the ‘service’ is doing when engaging with all the other backend services. Meaning, if you want to keep all of your Infrastructure and Policy as Code, you shouldn’t just be using the Control Tower Console.
You would use the Control Tower API for managing Controls / SCPs. That is if you don’t have any custom SCPs to deploy.
You would use the Service Catalog API for managing your accounts via CT Account Factory.
By using these things directly, your management Infrastructure and policies are not stored anywhere unless you document the API calls and controls you’ve enabled with them.
Are there tools?
There are tools to help you manage these items that require CT to be deployed first. My two favorites are:
-
Account Factory for Terraform (AFT)
-
Custom Customizations:
-
Built-in Customizations:
-
What if you are ‘like’ the reader with the question?
There is a point where you might have so many accounts and a process already, that you just write off ever using Control Tower. That is ok.
The best case is you have a small enough footprint where you can start with a Greenfield Organization and migrate accounts into the new Organization.
If you are sitting at a static number of accounts, you would have to decide as an organization if the juice is worth the squeeze for enrolling all of your existing accounts into a CT Landing Zone, only doing net-new accounts, or not bothering altogether.
When you (or the reader with the question) say “just putting the controls in Terraform” that is a whole lot different than a top-down governance model that leverages CT and Management account policies.
This places the controls external to the team’s visibility and workload.
Sure, you can deploy IAM policies and permissions boundaries at the account level, but then that opens the door for deviation from the standard and configuration of other ‘like’ accounts. CT can help deploy account types with compliance applied at the top.
Unless you are deploying SCPs with your Terraform to the Management Account (or by using a delegated account) you are managing all of your controls on a per-account configuration. Which can get messy and prone to error, inadvertent privilege escalation, or even self-induced DoS.
Going forward
AWS Control Tower is indeed a powerful solution that helps organizations govern their multi-account AWS environment with greater ease, security, and cost efficiency.
Side note on Cost ‘efficiency’
If you don’t properly configure your Landing Zone and the Default VPC settings, you are spending way more money by default because you are probably deploying a new VPC per account, and in every region placed under governance. In each of those regions, in every new account created by the account factory, NAT Gateways are getting deployed and sitting Idle.
Be sure to only enable regions you will have workloads and opt out of deploying the default VPC.
Control Tower costs about $50 a month by default before any additional configuration.
Just deploy Control Tower
With simplified account management, enhanced security and compliance, and cost optimization features, AWS Control Tower provides a comprehensive solution for managing your AWS environment.
If you’re looking to gain better visibility and control over your AWS accounts, AWS Control Tower is worth considering. Your workload and future compliance woes will benefit from it.
Hands down you will benefit from Control Tower if you ever have to worry about a 3rd party audit or any of the compliance frameworks regarding data storage and transmission.
Without actually seeing any of this in practice, it is really hard to see where you could benefit.
Where to get help
To help assist with this, I’m officially creating a course that will walk through how to configure a brand-new Greenfield Organization with Control Tower.
For more information on gaining early access to the course as well as getting more details about AWS Management and Governance, please subscribe to Unlimited Leave.
If you want to research more AWS-specific literature about why and how to deploy AWS Control Tower, take a look at the Cloud Foundation Team “Guidance for Establishing an Initial Foundation using control Tower AWS”. I’ll be talking more about this in the newsletter in the future.
If you have any questions or need direct assistance with your next AWS Control Tower deployment, please contact me.